Difference between Vulnerability Assessment and Penetration Testing (VAPT) and Cyber Visibility and Exposure (CVEQ™) Assessment
Unlike the one-time penetration tests (VAPT), the cyber visibility and exposure (CVEQ™) assessment enables simulation of various complex attack scenarios on your organisation. The assessment’s key value is that as opposed to penetration testing and gap analysis services, the platform runs ongoing testing of your Cybersecurity Posture. The approach enables you to assess the full scenario of a targeted attack against the entire organization, evaluating the organization’s capability to identify and respond to an attack, with a clear measure of the organization’s cyber Security visibility and exposure.
We have reviewed and analyzed over 200 local and global attacks (Fraud, IP theft and Sabotage) our assessment focuses on testing key capabilities that you need to have in pace to detect and respond against similar attacks.
Serianu’s Cyber Posture Assessment will provide you with a clear snapshot of your organization’s Cybersecurity posture with respect to internal capabilities to Anticipate, Detect, Respond and Contain threats.
Our unique perspective on Cyber risk
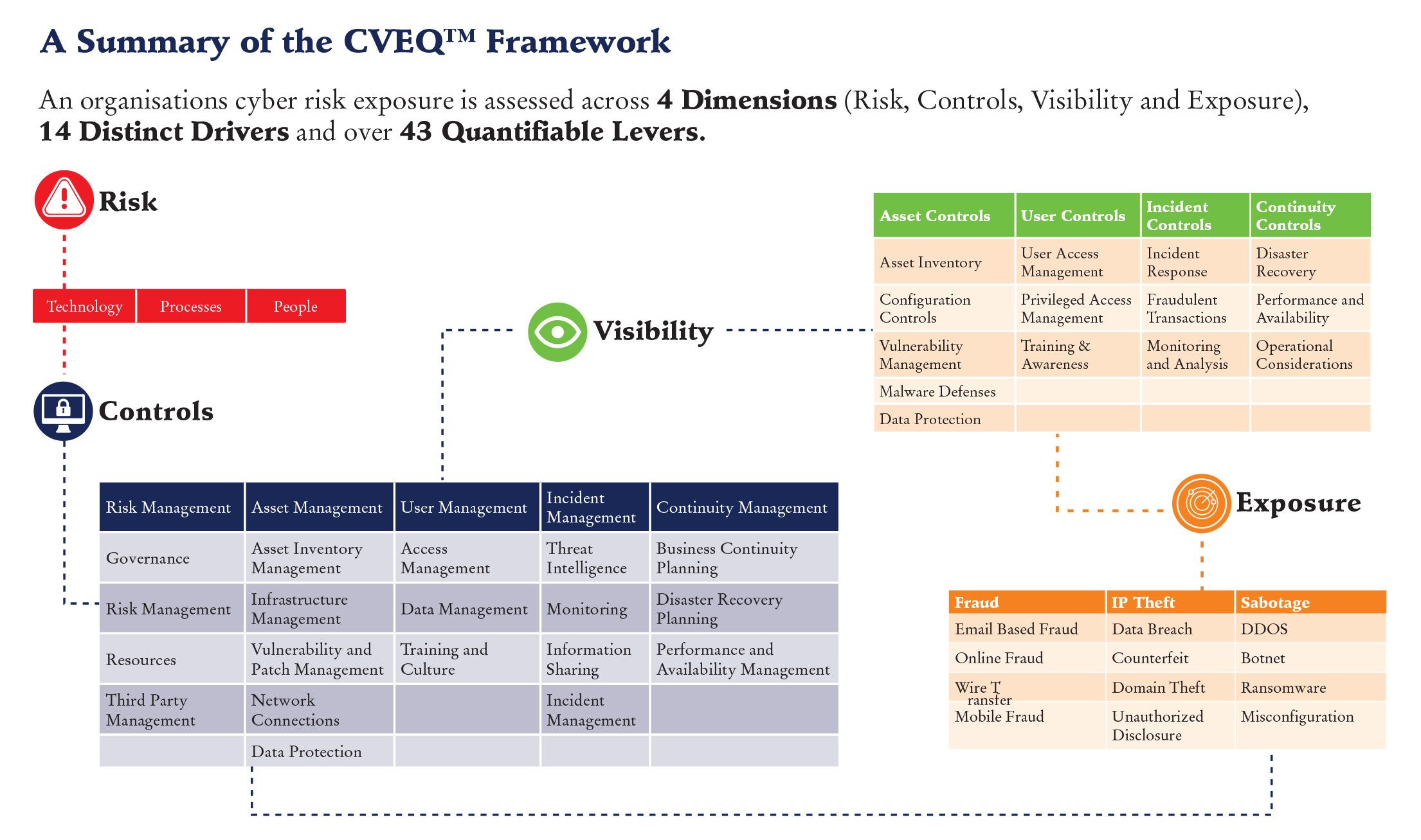
An organization’s cyber risk exposure is assessed across 6 dimensions, 14 distinct drivers and over 43 quantifiable levers.
- Cyber Risk Profile: Determines the risks that an organization’s activities, services, technologies, people, processes and products individually and collectively pose to the institution.
- Cyber Risk Appetite: Provides a set of metrics that are used to calculate internal capital requirements calibrated to the current cyber risk profile based on exposures (Fraud, IP Theft and Sabotage).
- Controls: This indicates how an institution’s behaviors, practices and processes support cybersecurity preparedness within the following five domains: risk management, asset management, user management, incident management and continuity management.
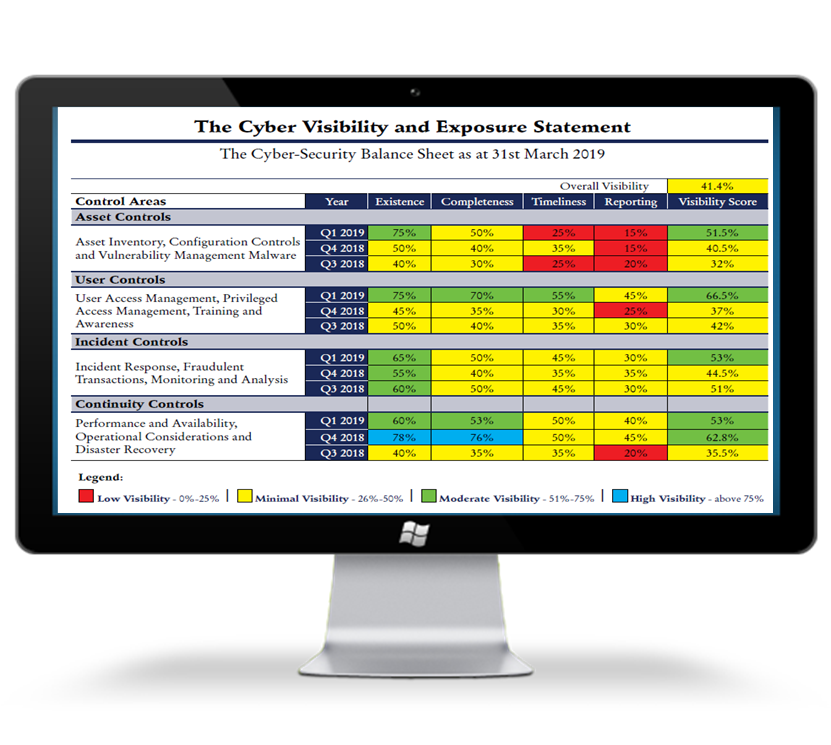
- Visibility: Visibility indicates the effectiveness and efficiency of implemented automated technical and process cyber security controls. It identifies how these controls are performing in the operational environment.
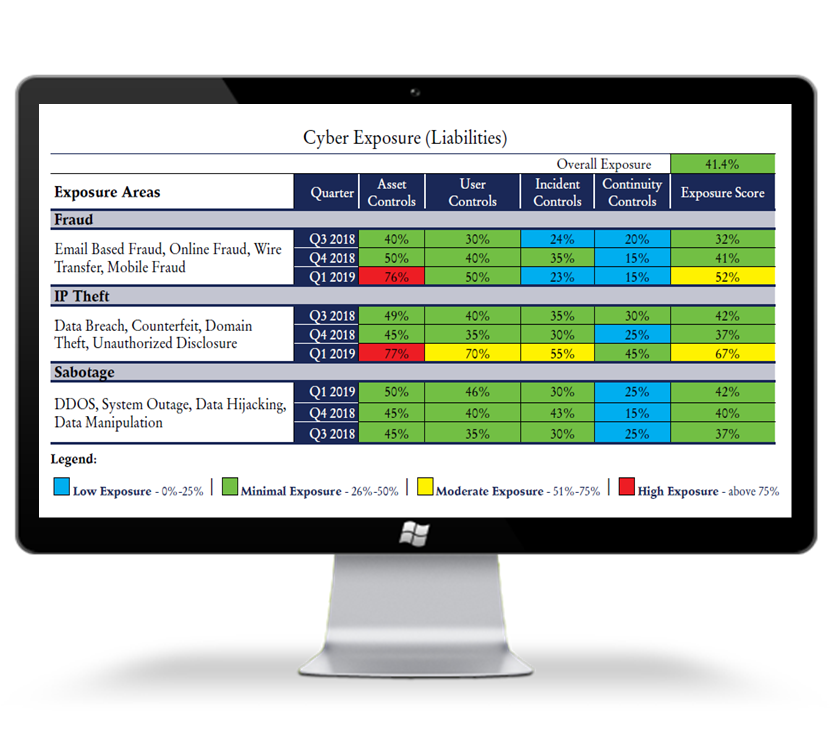
- Exposure: Cyber risk exposure is derived through analysis of an organization’s controls, industry data breach history and compromised dataset and more.
- Tolerance: Cyber Risk Tolerance refers to the maximum negative impact (loss amount) an organization is willing to accept from a specific risk event or series of risk events.
The Steps Involved
- Risk Profiling: Review the risks facing the organisation from People, process and technology perspective.
- Maturity Assessment and Benchmarking:Identify gaps based on regulatory requirements, industry standards and determine overall maturity. Compare these results with other peers within the industry.
- Visibility and Exposure Assessment: Use scientific measure, monitor and track visibility and exposure within the 4 main domains.
- Reporting and Remediation:Present final report including findings, recommendations and remediation roadmap.
Features
- Risk Profile Statement
- Risk Appetite Statement
- Maturity Statement
- Visibility Statement
- Exposure Statement
- Risk Tolerance Statement
