Network activity monitoring provides you with an overview of your entire network, and allows you to keep a constant eye on all network processes. You’ll always know if everything is okay with your network, or if something needs your attention. And that means you can react proactively to potential problems and prevent costly crashes.
Why Network Activity Monitoring ?
Help protect your business with highly effective threat detection and incident response services
Gain centralized security visibility across your critical cloud and on-premises environments
Move towards your security and compliance goals faster with less complexity and greater cost efficiency
Protect your security investment with a solution that scales and adapts to your changing business and IT environment
Benefits
- Available in the cloud
- High availability with built in Disaster Preparedness
- Real-time, Cross-correlated NOC and SOC analytics
- No IT resources/no Hardware Requirements
- Compliance Management and Reporting
- Rapid Real-time Threat Detection and Alerts
- No SIEM software upgrade headaches
- Integration with 3rd Party Ticketing Systems
- Implement a 24x7x365 NOC, SOC capabilities at a fraction of the cost.
Features
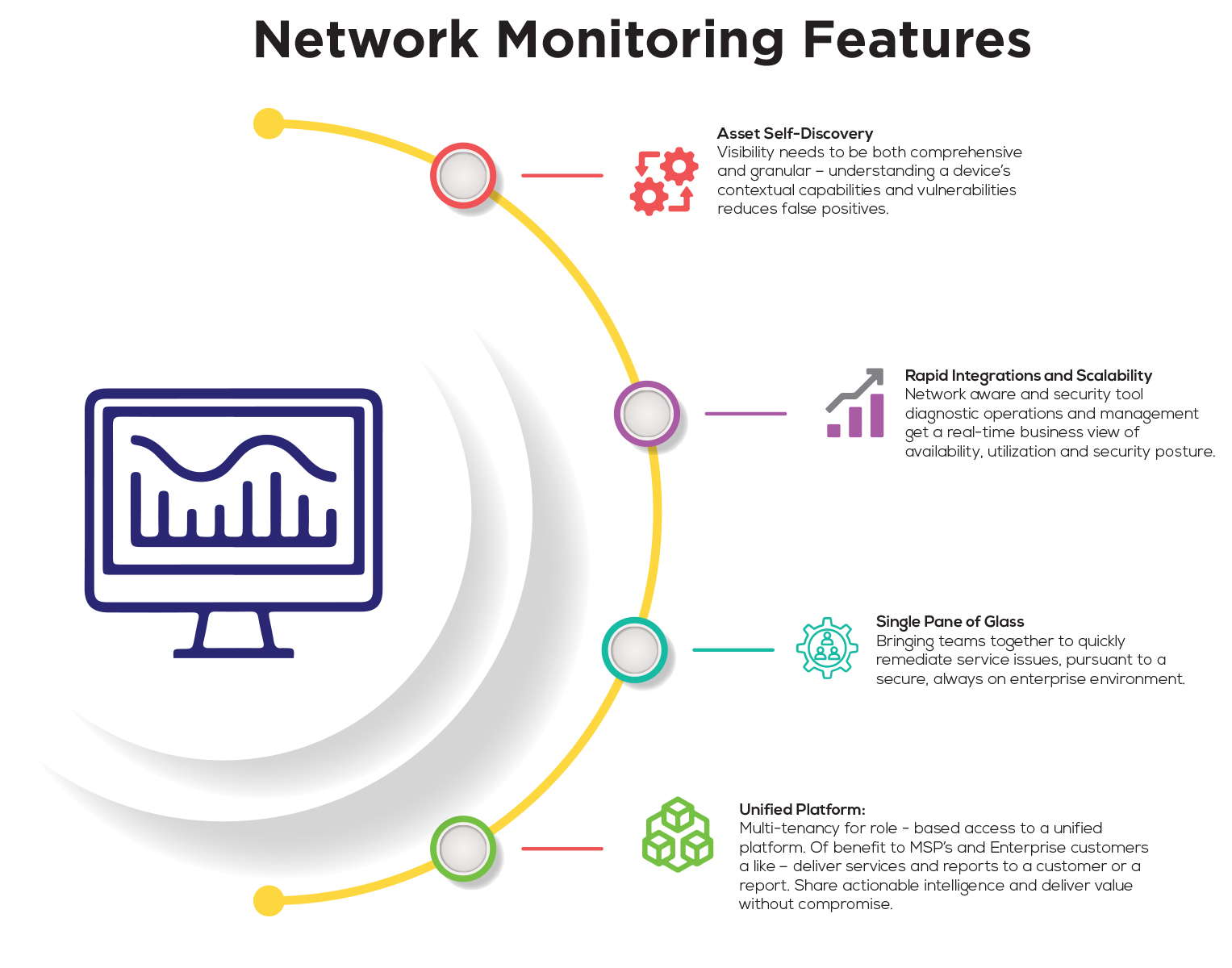
- Asset Self-Discovery: Visibility needs to be both comprehensive and granular – understanding a devices contextual capabilities and vulnerabilities reduces false positives.
- Rapid Integrations and Scalability: Network aware and security tool agnostic operations and management get a real-time business view of availability, utilization and security posture.
- Single Pane of Glass:Single Pane of Glass: Bringing teams together to quickly remediate service issues, pursuant to a secure, always on enterprise environment.
- Unified Platform: Multi-tenancy for role-based access to a unified platform. Of benefit to MSP’s and Enterprise customers alike – deliver services and reports to a customer or a report. Share actionable intelligence and deliver value without compromise.
UseCases
- Missing Patches
- Misconfigurations
- Malware
- Exploits
- Bandwidth utilization
- System Uptime
- Lateral Movement
- Privileged Escalation
- Privilege Activity Tracking
- Unauthorized Configuration changes
- Domain Changes
- Firewall changes
