Remediation is a daunting task when your team lacks the resources or expertise to implement and fix the reported gaps. Our remediation and implementation service provides on-demand, seasoned security experts to prioritize, implement, and execute the cyber security remediation plan.
Remediation Support
For groups looking for expert assistance in remediating audit gaps, Serianu’s remediation and implementation services provide assistance in achieving business requirements with compliance goals. This service covers security technology implementation, policy design, and configuration review.
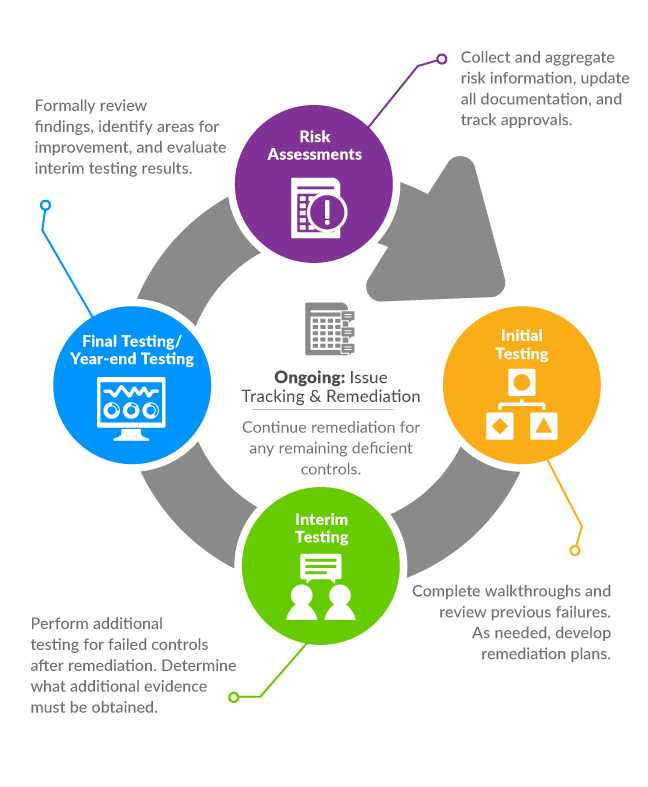
Remediation Process
We group process and control gaps into remediation projects based on the types and nature of mitigating controls (e.g. policies, standards, procedures, training and awareness and technical controls implementation). By collaborating with business and IT functions, we prioritize gaps that pose greatest risks and design a remediation roadmap.