At Serianu, we go beyond standard security practices to provide tailored solutions that secure critical assets and align with your business and IT strategies. Leveraging internationally recognized frameworks such as CVEQ (locally developed), NIST Cybersecurity Framework (CSF), ISO/IEC 27001, COBIT, and CIS Controls, we ensure your organization achieves compliance, resilience, and operational efficiency.
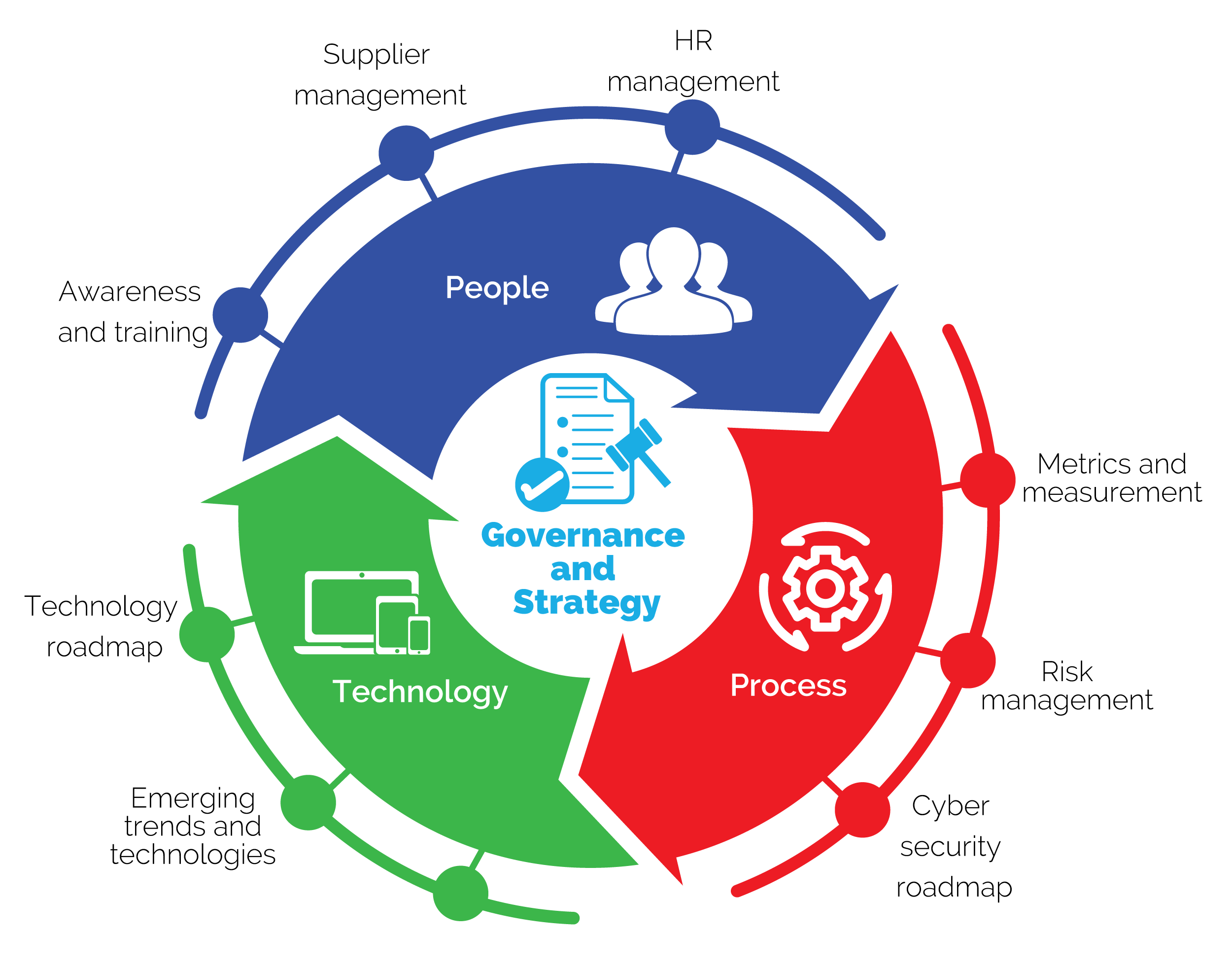
The service covers:
We use locally recovgnized frameworks such as CVEQ and globally recognized frameworks such as ISO/IEC 27001 and COBIT to deliver a robust governance structure that addresses compliance, operational goals, and risk management. Our services include:
- Alignment: Ensuring your information security and compliance efforts are fully integrated with your business and IT strategies, while meeting regulatory requirements.
- Threat Landscape Monitoring: Leveraging threat intelligence feeds aligned with NIST CSF to proactively address vulnerabilities and adapt to an ever-changing threat environment.
- Enhanced Communication Models: Promoting consistent decision-making and investment strategies by aligning with CIS Controls to address security risks effectively.
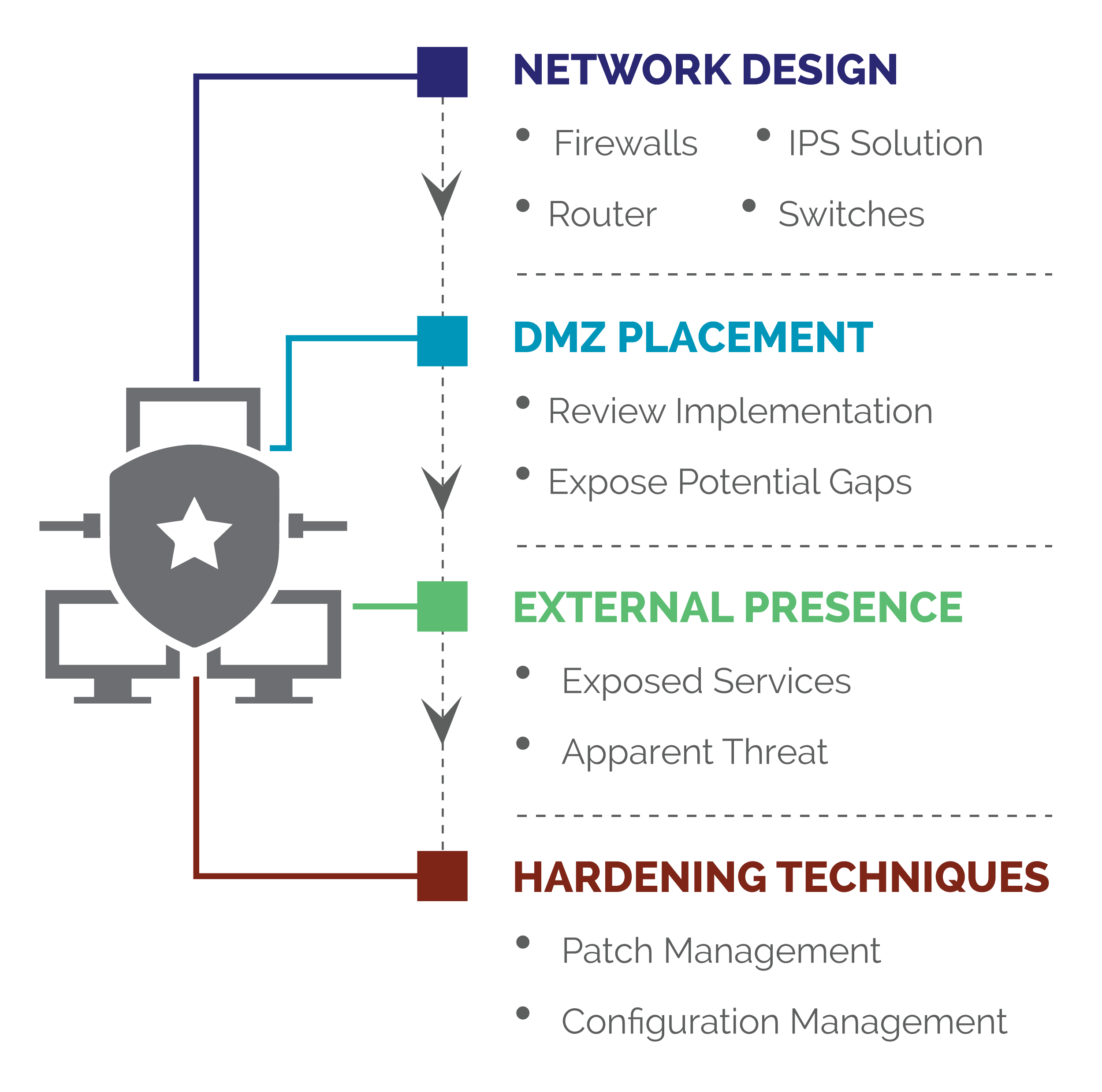
Using frameworks like CVEQ, MITRE ATT&CK and CIS Controls, we secure your network architecture by:
- Assessing your enterprise security architecture to ensure it meets business goals and risk management requirements.
- Identifying and remediating gaps in your network infrastructure to align with security frameworks and ensure robust defenses against threats.
- Implementing continuous monitoring solutions to safeguard your critical systems against potential intrusions.
We adopt a risk-based vulnerability management approach, leveraging frameworks such as OWASP Top Ten and CIS Controls to:
- Prioritize the identification and mitigation of vulnerabilities in critical systems and infrastructure.
- Conduct comprehensive risk assessments to ensure alignment with regulatory standards and industry best practices.
- Develop actionable remediation strategies that address identified threats efficiently and effectively.


With a focus on frameworks like ISO 22301 (Business Continuity Management), Serianu ensures your organization is prepared to recover and continue operations in the event of disruptions. Our services include:
- Creating and validating IT disaster recovery plans that are both practical and compliant with frameworks such as NIST SP 800-34.
- Ensuring recovery objectives are achievable while maintaining alignment with regulatory and business requirements.
- Providing tailored strategies to reduce downtime and ensure operational continuity during and after a disaster.
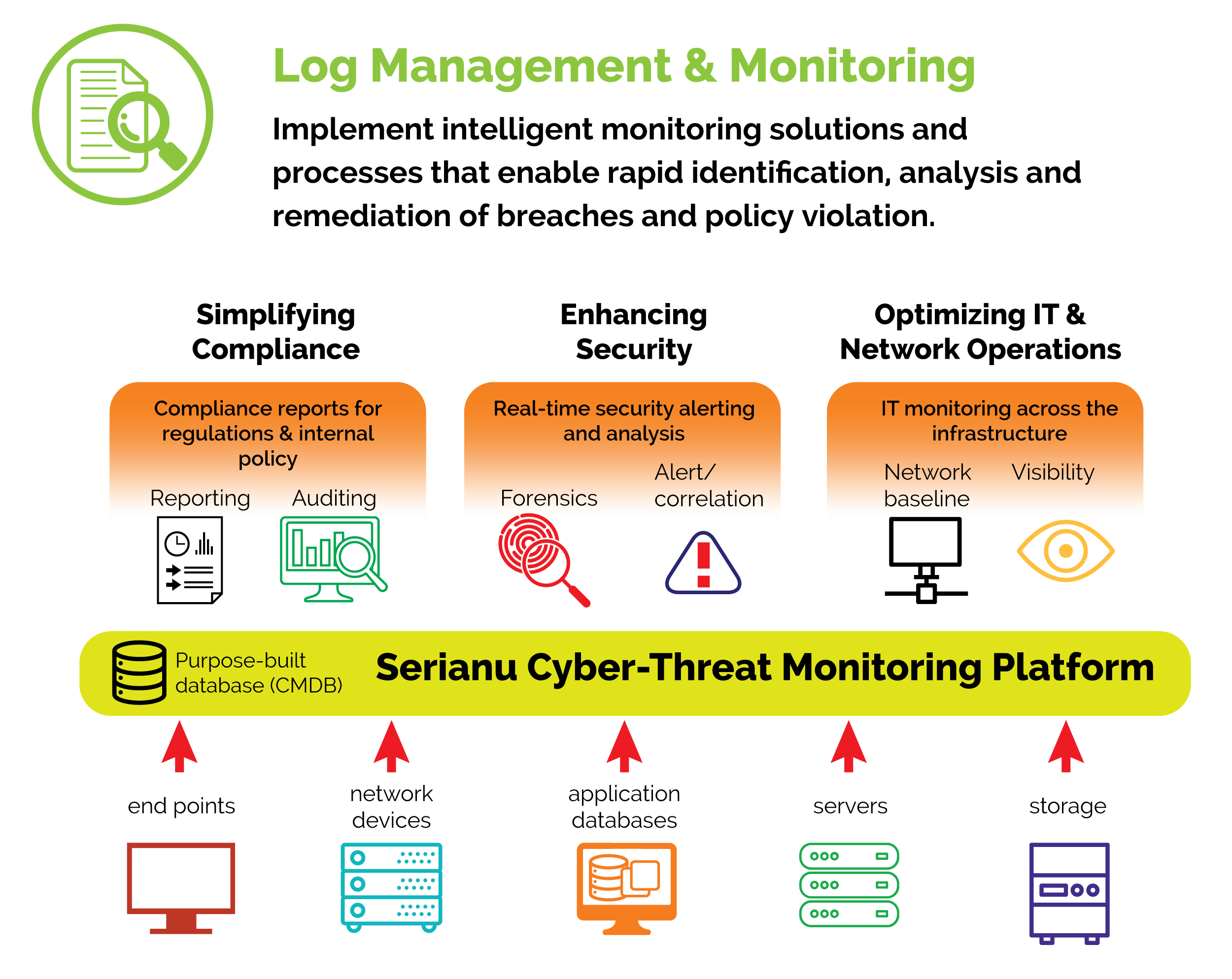
Effective log management is critical to detecting and responding to threats. Using frameworks like NIST CSF and MITRE ATT&CK, we:
- Implement intelligent monitoring solutions to rapidly identify suspicious activities and potential breaches.
- Automate log analysis and reporting for efficient incident response and regulatory compliance.
- Enhance breach detection and response capabilities through advanced log management aligned with industry standards.

With an emphasis on protecting sensitive data, we help organizations implement privacy and data protection controls aligned with regulations such as GDPR, CCPA, and frameworks like ISO/IEC 27701:
- Data Inventory and Classification: Identifying and classifying sensitive data to ensure its proper handling and protection.
- Privacy Impact Assessments (PIAs): Conducting assessments to understand and mitigate risks to personal data.
- Data Encryption and Access Controls: Implementing robust encryption protocols and access restrictions to safeguard data integrity and confidentiality.
- Regulatory Compliance: Ensuring your data management practices comply with privacy laws and frameworks, including GDPR and NIST Privacy Framework.
Aligned with local and global frameworks such as CVEQ, NIST 800-63 (Digital Identity Guidelines) and ISO/IEC 27002, our IAM services include:
- Securing sensitive systems by restricting access to authorized personnel.
- Reviewing internal processes to eliminate risks such as user segregation issues, insider threats, and vendor access risks.
- Implementing and auditing IAM policies to comply with global best practices and regulatory requirements.

